Digital identity security focuses on protecting identities, credentials, and access mechanisms that regulate how users and systems interact with critical infrastructure. This article outlines the core principles of digital identity security, its role in reducing attack surfaces, and why it’s fundamental to securing modern IT operations.
Digital identity security refers to the protection of digital identities and user credentials across systems, services, and platforms. It ensures secure access, authentication, and authorization to mitigate risks like identity theft, data breaches, and unauthorized access.
Digital identity management is crucial because weak or mismanaged identities can lead to breaches, unauthorized access, and data loss. Strong security ensures only the right users access the right resources.
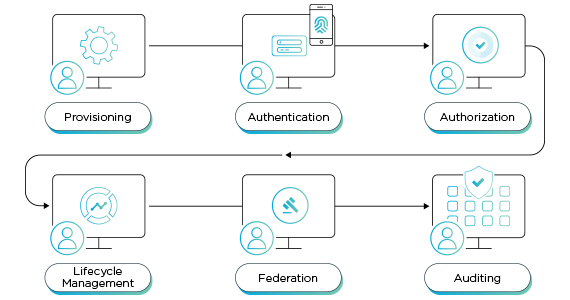
Source: One Identity
Digital identities help secure cloud applications, endpoints, and data centers by associating users and systems with unique credentials. Managing these identities effectively is key to reducing attack surfaces and maintaining enterprise security posture.
Effective identity management solutions automate account provisioning, enforce least privilege, and simplify credential lifecycle management. By integrating with directory services like LDAP or Microsoft Active Directory, they provide a centralized and scalable architecture.
Modern identity solutions include support for federated identity, smart card login, and token-based authentication to protect against cyber attacks. These solutions often comply with industry standards like HIPAA, PCI, and NIST for enterprise compliance.
Digital identity systems face multiple cyber threats that exploit authentication weaknesses, compromised credentials, and inadequate access controls. Here’s a breakdown of the most common types:
Attackers gain access to privileged accounts (PAM system) by bypassing or exploiting weak identity and access management policies. Once inside, they can escalate privileges and move laterally within IT systems, often undetected. Corporate account takeover is especially dangerous when admin accounts are compromised.
Credential stuffing is when automated bots use breached username-password pairs from previous leaks to access systems using single sign-on or cloud-based applications. Without strong authentication and centralized access governance, organizations remain vulnerable.
In password spraying, attackers try common passwords across many user accounts, targeting weak or reused credentials. This method evades lockout mechanisms and highlights the need for secure lifecycle practices and robust identity management systems.
Implementing strong authentication, encryption, privileged access controls, and access governance helps organizations secure identities and mitigate the risks highlighted by Gartner and other cybersecurity frameworks.
Identity plays a critical role in access governance, especially in cloud-based infrastructures where traditional perimeter defenses are obsolete. Cloud security solutions rely on identity services and access rights enforcement to protect data privacy and secure remote access.
Identity and Access Management (IAM) controls who can access what in your systems. It secures user identities, enforces authentication, and manages permissions to reduce the risk of breaches.
This includes enforcing access policies through identity federation, strong authentication, and privilege-based access rules.
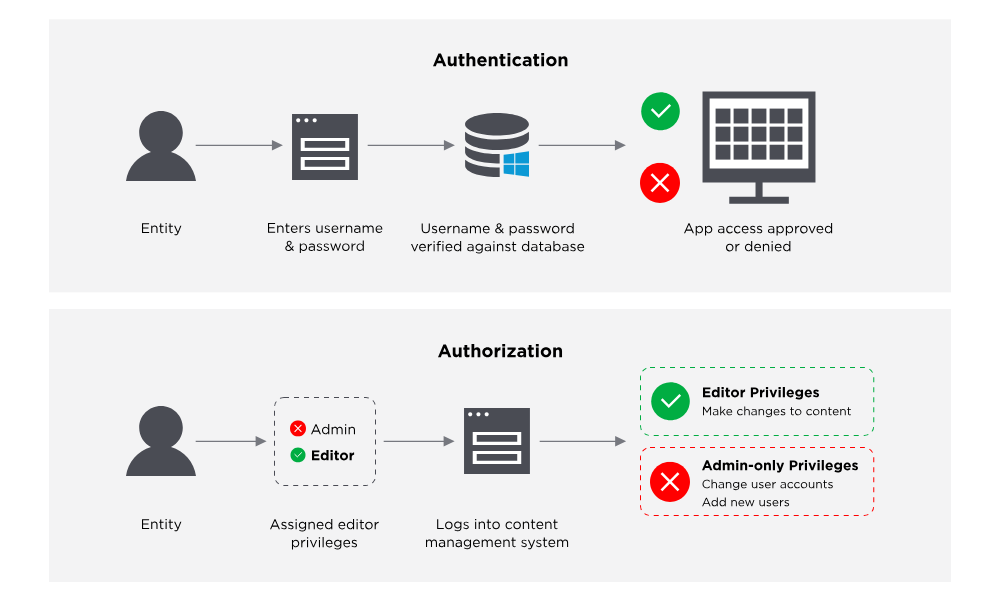
Source: OneLogin
Companies need IAM to:
In cloud computing, data security depends on secure provisioning, identity federation, and identity lifecycle auditing. These controls help prevent unauthorized access and ensure security and compliance in SaaS and IaaS environments.
For example, SaaS Security Posture Management (SSPM) is a cloud security function that continuously monitors and secures SaaS configurations. Alongside Cloud Infrastructure Entitlement Management (CIEM) and Cloud Security Posture Management (CSPM), these tools form a core part of modern cybersecurity strategies—helping integrate and govern identities across applications, devices, cloud, and on-premise systems.
Selecting an identity security platform depends on support for strong authentication, federated access, and secure user management across cloud and on-premise systems. Platforms should also support identity federation, endpoint security, and automated lifecycle workflows.
Below are 10 leading providers of digital identity security, evaluated based on three core buying criteria:
| Rank | Company | Identity Governance | Integration & Compatibility | Deployment & Scalability |
| 1 | One Identity | Strong governance framework with role-based access control | Native integration with AD, Azure AD, SAP, and Unix | Modular and scalable architecture for hybrid IT |
| 2 | Okta | Full lifecycle identity management with policy enforcement | Industry-best app and API integration ecosystem | Cloud-native platform with elastic scaling |
| 3 | CyberArk | Enterprise-grade privileged access and governance controls | Seamless with DevOps pipelines and hybrid cloud | Built for secure, large-scale enterprise operations |
| 4 | Microsoft Entra | Tight identity governance within Microsoft ecosystem | Flawless integration with Azure, M365, and Windows | Natively scalable across Microsoft cloud services |
| 5 | Ping Identity | Adaptive access control with strong federated ID governance | Broad protocol support (OIDC, SAML, SCIM, etc.) | Scales well for both workforce and customer IAM use |
Compliance requirements such as GDPR, HIPAA, and SOX are driving organizations to adopt identity governance and auditing capabilities. Security solutions must also support logging, reporting, and remediation of vulnerabilities to meet industry standards.
Emerging trends include the use of blockchain for decentralized identity, biometrics for secure authentication, and AI for threat detection and user behavior analysis. These innovations aim to reduce the attack surface and strengthen proactive identity governance.
Put your brand and expertise in the spotlight with one of our carefully crafted sponsorship packages. Whether it be a speaking role, a delegate package for your team, logo exposure, or the opportunity to bring your current and potential clients along to the event, we have got you covered with something that will genuinely help you get deals done at our events.
Join us in uniting for a safer tomorrow!
